Use AppLocker to Gain Control Over Desktop Applications
This guide explains how to take advantage of AppLocker, a tool that enables strict control over desktop applications, for improved endpoint security.
July 10, 2023

Security-conscious organizations must pay careful attention to the applications that run on network endpoints. Unauthorized applications can introduce security vulnerabilities and expose the organization to licensing violations. They can also disrupt system stability or cause support issues. Needless to say, it is important to maintain tight control over the applications installed on users’ PCs.
This is where AppLocker comes into play.
AppLocker is a native tool integrated into the Windows operating system. AppLocker enables IT pros to create policies that control which applications can run on a Windows endpoint. In addition to blocking unauthorized software, AppLocker can facilitate the transition to new application versions by preventing the execution of older versions. IT pros can also use AppLocker to permit certain user groups to run an application while restricting others from running that same application, even on shared PCs. Although AppLocker was not intended to replace dedicated malware prevention software, some organizations use it as an additional layer of defense against malware infections.
While there are third-party alternatives to AppLocker, the better options often come with hefty price tags, whereas AppLocker can be used without incurring additional licensing costs.
AppLocker is relatively easy to set up. However, it can be difficult to create policies that strike the right balance between restrictiveness and permissiveness.
As such, this guide will cover AppLocker’s fundamental concepts and best practices for crafting effective policies.
How To Access AppLocker
With that said, AppLocker is built into group policy. You can access AppLocker through the Group Policy Management Editor by following this path: Computer Configuration > Policies > Windows Settings > Security Settings > Application Control Policies > AppLocker. Figure 1 displays the main interface of AppLocker.

AppLocker 1-1
Figure 1. The interface of AppLocker.
Before proceeding, it’s important to understand that an incorrect AppLocker setup can cause a lot of problems. To avoid issues, I strongly recommend experimenting with AppLocker in an isolated lab environment first (more on this below). When you’re ready to implement AppLocker in a production environment, create a backup as a precautionary measure in case anything goes wrong.
Understanding AppLocker Rules
The basic structure used by AppLocker is relatively simple. Application control is based on rules. These rules are organized into five rule collections, four of which are displayed above in Figure 1. These include executable rules, Windows installer rules, script rules, and packaged app rules. The rule collection not shown in Figure 1 is DLL rules.
Executable rules
Executable rules pertain to executable files and can identify specific executables based on their publisher (if digitally signed), file path, or file hash.
Windows installer rules
Windows installer rules function similarly to executable file rules. Whereas executable files focus on .EXE files and other executable file types, Windows installer rules pertain to MSI files (Windows installer packages). Windows installer rules can also be based on the publisher, file path, or file hash.
Script rules
Script rules operate similarly to other rule types, but they pertain to script files such as PowerShell scripts, batch files, VBScript, JavaScript, and .CMD files. Keep in mind that script rules solely apply to script files and do not prevent fileless scripts. They also do not prevent users from manually executing commands in PowerShell.
Packaged app rules
Packaged app rules serve a similar purpose to Windows installer rules, except they apply to packaged apps or their installers instead of MSI files.
DLL rules
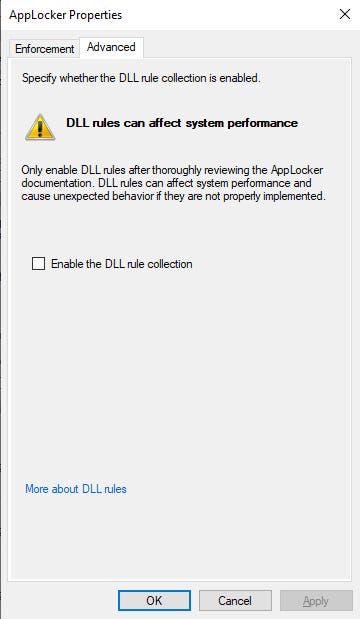
There is a fifth type of AppLocker rule called a DLL rule. However, DLL rules are hidden due to their potential to disrupt Windows functionality and degrade system performance. If you need to create a DLL file, click the Configure Rule Enforcement link shown in Figure 1. From there, go to the Advanced tab and follow the instructions shown in Figure 2 to enable DLL rules.
AppLocker 1-2
Figure 2. DLL rules can be found on the Advanced tab of the AppLocker Properties dialog box.
In general, creating a rule in AppLocker follows a simple process. First, you decide whether you want to create an allow or deny rule and then specify who the rule will apply to. Next, you set the rule’s conditions by selecting criteria such as the file’s publisher, path, or file hash. Additionally, you can define any exceptions to the rule.
As simple as this process may seem, some rather significant gotchas can come into play when creating rules. In the remainder of the article, I will discuss best practices that can help you avoid common issues associated with AppLocker.
Setting up a Lab Environment
As mentioned earlier, it’s important to start by configuring AppLocker in a lab environment. Once you are sure your AppLocker rules work properly, you can then move to a production environment.
This involves setting up physical or virtual machines that mimic the configuration of your production desktops. During this setup, make sure to install the same software (and updates) used in production while removing any unnecessary Windows components.
Building a model PC serves two purposes: making it easier to test your AppLocker configuration and enabling automatic rule generation based on the installed software.
Set Rule Enforcement to Audit Only Mode
The very first thing you must do on your model PC (besides making a backup in case something goes wrong) is configure AppLocker rule enforcement.
To ensure that AppLocker rules are implemented correctly without causing unintended consequences and system lockdowns, you must set rule enforcement to audit mode. This allows you to evaluate how AppLocker interprets the rules without fully implementing them.
To do this, follow these steps:
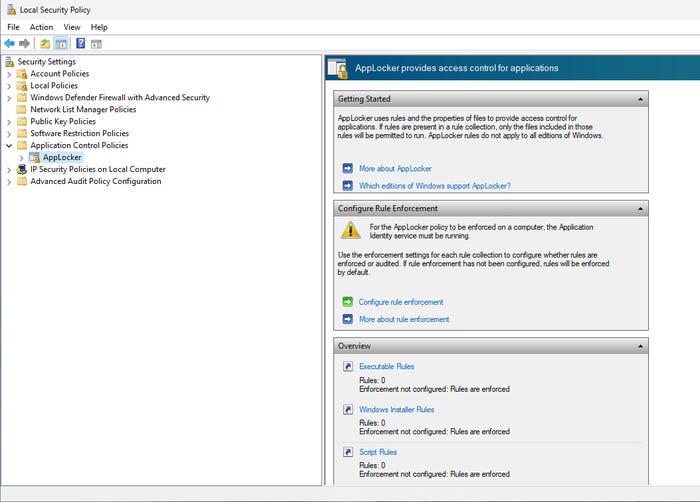
Open the Local Security Policy on your model PC.
Select the AppLocker option within the policy settings.
Click on the 'Configure rule enforcement' link (see Figure 3) to open the AppLocker Properties sheet.
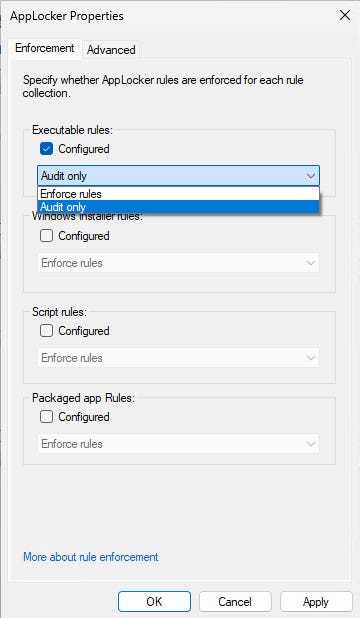
In the AppLocker Properties sheet, select the Configured checkbox for each rule collection.
Set the enforcement option to 'Audit only' (see Figure 4).
Repeat the above steps for all rule collections.
Finally, click OK to save and finalize the configuration.
With Audit Mode enabled you can safely assess the impact of AppLocker rules on your model PC.
AppLocker 2-1
Figure 3. Accessing AppLocker through the Local Security Policy on a PC.
AppLocker 2-2
Figure 4. Setting AppLocker to use Audit Only mode for rule enforcement.
Automatically Generate Rules
Next, you can automatically generate rules based on the software already installed on your model PC.
To do so, follow these steps:
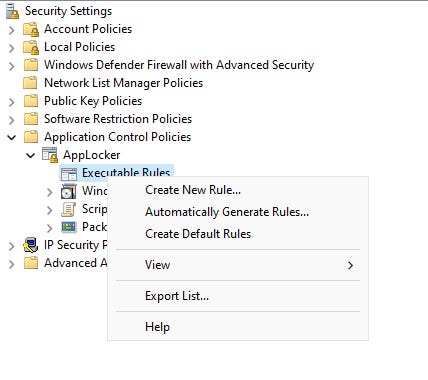
Right-click on a rule collection to open the shortcut menu and select the Automatically Generate Rules option (as shown in Figure 5).
Windows will display the Automatically Generate Rules dialog box. It will prompt you to specify who the rule will apply to, the folder containing the files to analyze, and the name that you want to use to identify the rule set. These options are populated automatically but can be modified if needed.
AppLocker 2-3
Figure 5. Right-click on a rule collection and select the Automatically Generate Rules option.
Click Next to go to the rule preferences screen. By default, the preferences are set to create publisher rules whenever possible, with file hash rules as a backup. You can adjust these preferences to suit your requirements.
Click Next, and Windows will analyze your files, providing a summary of the rules to be generated. Before clicking Create, it is a good idea to first click the link that says, 'View rules that will be automatically created.' This lets you review what is about to happen. As you can see in Figure 6, the rule summary includes a search box for specific rule lookups.
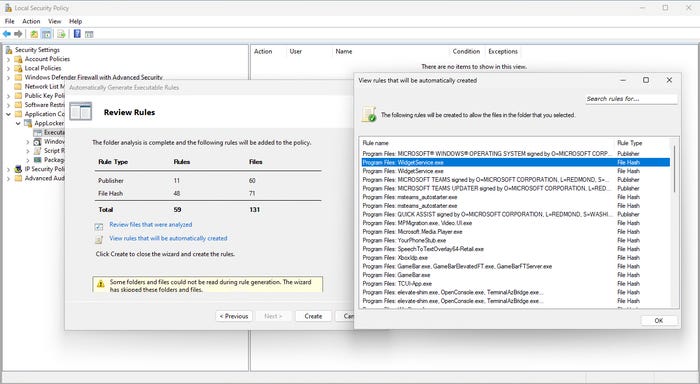
AppLocker 2-4
Figure 6. Review the automatically generated rules before they are created.
After reviewing the rules, click Create. A message will appear, asking if you want to create the default rules, as well. It is extremely important to allow the creation of default rules to ensure the proper execution of critical system files.
Once the automatic rule generation process is complete, go back and generate any additional rules as necessary. For example, you may need to generate Windows installer rules or rules for programs located in other folders. At a minimum, consider automatically generating rules for the C:Program Files (x86) folder.
It’s entirely possible that rules generated automatically may be overly permissive. If you see a rule that you do not like, you can delete it.
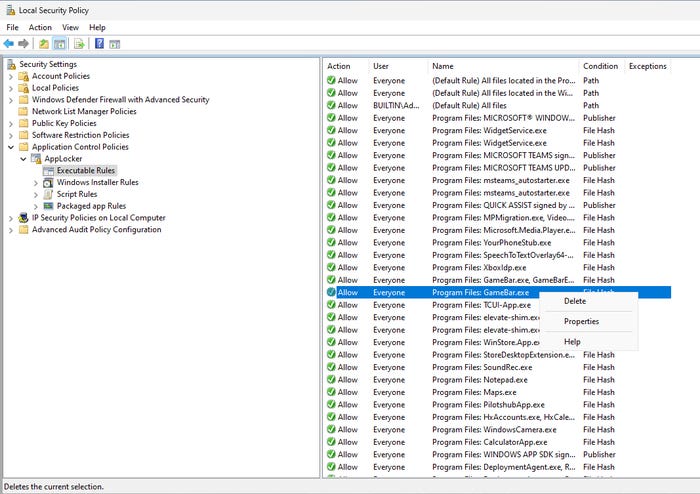
AppLocker 2-5
Figure 5. Remove rules that don’t fit your needs.
To delete a rule, right-click on the rule and select the Delete command from the shortcut menu, as shown in Figure 5.
Test and Export Your Rules
Perform thorough testing to further validate and prepare your AppLocker rules for implementation. It’s important to confirm that the rule collection works as intended before enabling rule enforcement.
Once you are satisfied that your rule collection works, you can avoid manually recreating it in the production environment. Instead, export the rules from your lab environment and import them into the production environment.
When importing rules to the production environment, be sure to initially set the environment to use audit mode. There is a slight chance that the rules may behave differently in the production environment. Using audit mode, you can closely monitor and ensure the rules function correctly before enforcing them fully.
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
