I recently presented research information at one of SQL Server Magazine's "Managing Your Cross-Platform Data" roadshows and got the chance to hear from several Oracle DBAs about their perceptions of SQL Server 2005 and SQL Server 2005 Express. I know that Oracle DBAs view Oracle as a superior product, so I wasn't surprised that these DBAs had a low opinion of SQL Server. After all, if you pay as much for a product as their companies did, it's only natural that you'd rally behind that product. However, what did surprise me was the common set of reasons behind their opinions: stability and security. Their perception is that SQL Server and SQL Server Express aren't stable databases--and thus not ready for enterprise work--primarily because they run on the Windows OS. They also said they believe that SQL Server 2005 and SQL Server 2005 Express aren't secure because these products have been hit with viruses such as the now infamous SQL Slammer worm that hit SQL Server and Microsoft SQL Server Desktop Engine (MSDE) databases in early 2003. In my opinion, these thoughts are misconceptions based on ancient history and aren't relevant to the current SQL Server 2005 and SQL Server Express products.
Older versions of Windows 9x were plagued by stability problems, but that isn't the case with Windows XP and Windows Server 2003 OSs. Historically, desktop systems have had more problems than servers because of the varied software they run, the multiple device drivers they must support, and user error. But like everything else, even desktop systems have improved over the years. And the same problems affect other desktop databases--such as Oracle Express, DB2 Express, and even MySQL--just as much as they affect SQL Server Express.
Clearly, SQL Slammer significantly harmed the reputation of SQL Server products, so much so that it might take Microsoft a decade to live it down. Never mind that Microsoft had a patch available for SQL Slammer months before the exploit or that organizations that had correctly configured their firewalls and shut down all the unnecessary access to port 1433 weren't affected by SQL Slammer. Perhaps one of the unexpected outcomes of the exploit was to point out how widespread the adoption of MSDE had become because it was primarily those unknown and unpatched MSDE installations that facilitated the rapid spread of the exploit.
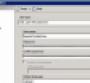
Today, SQL Server Express takes a totally different approach to security than MSDE did. First, because of Microsoft's Security Initiative, the SQL Server Express code has been through a more thorough review than SQL Server 2000 and MSDE, and fixes for the older security exploits have been incorporated into SQL Server Express. Next, the original versions of MSDE shipped with all network access enabled after installation. SQL Server 2005 Express takes the opposite tack and by default, all network access is completely shut down, which completely eliminates the possibility of anything like the SQL Slammer exploit. If you want network access to a SQL Server Express database, you need to enable it by using the SQL Server Surface Area Configuration Tool. Nowadays, stability and security are a given with SQL Server 2005 and SQL Server Express.
Although security was certainly a topic that came up in my roadshow sessions, the real focus of the ongoing SQL Server-Oracle road shows is database integration. If you're interested in Windows and Linux integration or you want to learn more about virtualization, you should check out the upcoming TechX World road shows at
      http://www.techxworld.com/registration/index.cfm?fuseaction=dynamic&v=0&p=5061&code=/?code=rdshw
I'll be one of the guest speakers, and I'll be talking about virtualization technologies.