Despite the growth in DevSecOps adoption in recent years, there are significant gaps in securing cloud deployments, according to a new report.
Datadog has released its State of DevSecOps 2024 report, unveiling key insights into the adoption of DevSecOps practices and the challenges organizations face in securing cloud deployments.
The report's top findings include:
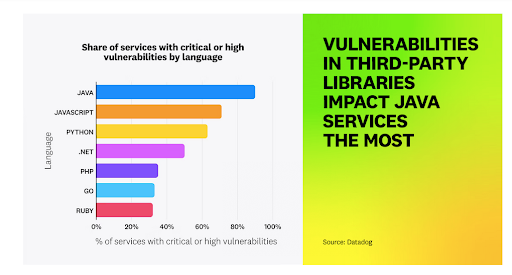
- Java services are the most impacted by third-party vulnerabilities, with 90% vulnerable to critical or high-severity issues.
- Attacks from automated security scanners generate substantial noise, with only 0.0065% successfully triggering a vulnerability.
- The usage of short-lived credentials in CI/CD pipelines remains low, posing security risks.
"The only thing that DevSecOps teams can really get wrong is not continuously improving and iterating quickly," Andrew Krug, head of security advocacy at Datadog, told ITPro Today. "When something isn’t working, they need to identify it as early as possible and act. Having the right signals to be data-informed is also key to making those decisions."
Vulnerability Landscape: Java Services in the Crosshairs
The report found Java services the most vulnerable to third-party vulnerabilities, with 90% affected by critical or high-severity issues introduced by external libraries.
Additionally, 55% of Java services are impacted by vulnerabilities actively exploited by threat actors, according to the U.S. Cybersecurity and Infrastructure Security Agency's (CISA) Known Exploited Vulnerabilities (KEV) catalog.
As to why Java is being impacted so much, Krug argues that popularity is a key factor.
"We could spend a lot of time debating the pros and cons of various programming languages and how design patterns lead to vulnerability introduction," Krug said. "Quite frankly, though, attackers are simply targeting Java applications due to the popularity of the language and its heavy use in the enterprise. Java as a language is no more or less secure than any other.”
Noise Reduction and Prioritization Crucial for Effective Security
While organizations face numerous vulnerability alerts, the report emphasizes the importance of prioritization frameworks.
Datadog found that attacks from automated security scanners, while generating a large volume of alerts, rarely result in successful exploitation, with only 0.0065% of attempts triggering vulnerabilities.
Furthermore, the report suggests that, based on adjusted scoring methodologies that consider factors such as public exposure, production environment, and availability of exploit code, only a small portion of identified vulnerabilities are worth prioritizing.

Krug noted that a significant number of organizations were able to either highly prioritize or find that they did not need to act on a vulnerability once they took runtime context into account.
"This shows a clear value of running security tools in development, test, and production environments that are adding more signal to the picture and helping engineering teams know exactly what to prioritize next," he said.
Short-Lived Credentials in CI/CD: Room for Improvement
The report also highlights the importance of using short-lived credentials in CI/CD pipelines to mitigate the risk of data breaches caused by credential leaks.
However, the findings indicate that this practice is still not widely adopted. Among organizations using GitHub Actions in AWS, only 37% exclusively use keyless authentication based on short-lived credentials and OpenID Connect (OIDC), while 63% use long-lived IAM users at least once.
"Seeing increased adoption of the ability to use short-lived or just-in-time credentials in CI/CD is going to be one of those things we continue to stress," Krug said. "Historically, attackers will go after CI/CD systems simply because they know the keys to the kingdom are there if those systems form resources."
About the author
 Sean Michael Kerner is an IT consultant, technology enthusiast and tinkerer. He consults to industry and media organizations on technology issues.
Sean Michael Kerner is an IT consultant, technology enthusiast and tinkerer. He consults to industry and media organizations on technology issues.




